Key Takeaways
- Install nmap if you don’t already have it on your Linux computer. Run “sudo apt-get install nmap” on Ubuntu, or “sudo dnf install nmap” on Fedora.
- Use nmap to scan your network and discover the IP addresses of connected devices. You can perform a quick scan (-sn option) or a deeper scan that includes probing the ports on the devices.
Think you know what’s connected to your home network? You might be surprised. Learn how to check using nmap on Linux, which will let you explore all the devices connected to your network.
You might think your home network is pretty simple, and there’s nothing to be learned from having a deeper look at it. You might be right, but the chances are you’ll learn something you didn’t know. With the proliferation of Internet of Things devices, mobile devices such as phones and tablets, and the smart home revolution — in addition to “normal” network devices such as broadband routers, laptops, and desktop computers — it might be an eye-opener.
If You Need To, Install nmap
We’re going to use the nmapcommand. Depending on what other software packages you have installed on your computer, nmap might be installed for you already.
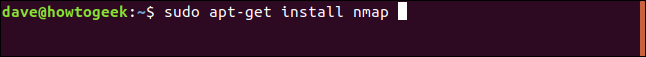
If not, this is how to install it in Ubuntu.
sudo apt-get install nmap
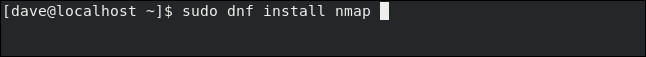
This is how to install it on Fedora.
sudo dnf install nmap
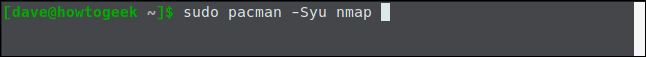
This is how to install it on Manjaro.
sudo pacman -Syu nmap
You can install it on other versions of Linux using the package manager for your Linux distributions.
Find Your IP Address
The first task is to discover what the IP address of your Linux computer is. There is a minimum and a maximum IP address your network can use. This is the scope or range of IP addresses for your network. We will need to provide IP addresses or a range of IP addresses to nmap, so we need to know what those values are.
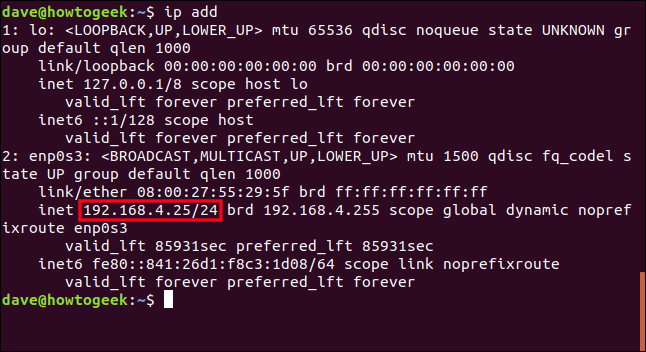
Handily, Linux provides a command called ip and it has an option called addr (address). Type ip, a space, addr, and press Enter.
ip addr
In the bottom section of the output, you will find your ip address. It is preceded by the label “inet”.
The IP address of this computer is “192.168.4.25”. The “/24” means that there are three consecutive sets of eight 1’s in the subnet mask. (And 3 x 8 =24.)
In binary, the subnet mask is:
11111111.11111111.11111111.00000000
and in decimal, it is 255.255.255.0.
The subnet mask and the IP address are used to indicate which part of the IP address identifies the network, and which part identifies the device. This subnet mask informs the hardware that the first three numbers of the IP address will identify the network and the last part of the IP address identifies the individual devices. And because the largest number you can hold in an 8-bit binary number is 255, the IP address range for this network will be 192.168.4.0 through to 192.168.4.255.
All of that is encapsulated in the “/24”. Happily, nmap works with that notation, so we have what we need to start to use nmap.
Get Started with nmap
nmap is a network mapping tool. It works by sending various network messages to the IP addresses in the range we’re going to provide it with it. It can deduce a lot about the device it is probing by judging and interpreting the type of responses it gets.
Let’s kick off a simple scan with nmap. We’re going to use the -sn (scan no port) option. This tells nmap to not probe the ports on the devices for now. It will do a lightweight, quick scan.
Even so, it can take a little time for nmap to run. Of course, the more devices you have on the network, the longer it will take. It does all of its probing and reconnaissance work first and then presents its findings once the first phase is complete. Don’t be surprised when nothing visible happens for a minute or so.
The IP address we’re going to use is the one we obtained using the ip command earlier, but the final number is set to zero. That is the first possible IPAddress on this network. The “/24” tells nmap to scan the entire range of this network. The parameter “192.168.4.0/24” translates as “start at IP address 192.168.4.0 and work right through all IP addresses up to and including 192.168.4.255”.
Note we are using sudo.
sudo nmap -sn 192.168.4.0/24
After a short wait, the output is written to the terminal window.
You can run this scan without using sudo, but using sudo ensures it can extract as much information as possible. Without sudo this scan would not return the manufacturer information, for example.
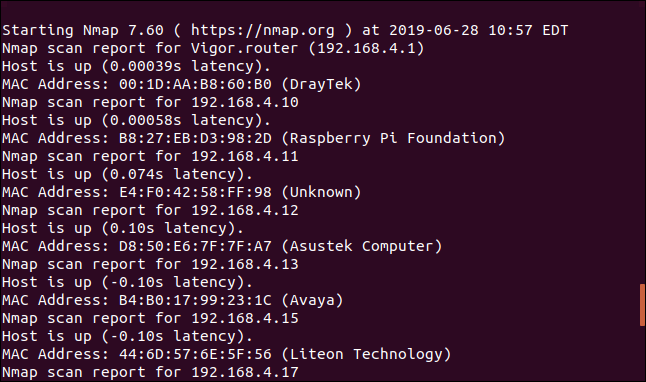
The advantage of using the -sn option — as well as being a quick and lightweight scan — is it gives you a neat list of the live IP addresses. In other words, we have a list of the devices connected to the network, together with their IP address. And where possible, nmap has identified the manufacturer. That’s not bad for the first try.
Here’s the bottom of the list.
We’ve established a list of the connected network devices, so we know how many of them there are. There are 15 devices switched on and connected to the network. We know the manufacturer for some of them. Or, as we shall see, we have what nmap has reported as the manufacturer, to the best of its ability.
When you look through your results, you will likely see devices that you recognize. There may well be some that you don’t. These are the ones we need to investigate further.
What some of these devices are is clear to me. Raspberry Pi Foundation is self-explanatory. The Amazon Technologies device will be my Echo Dot. The only Samsung device I have is a laser printer, so that narrows that one down. There’s a couple of devices listed as manufactured by Dell. Those are easy, that’s a PC and laptop. The Avaya device is a Voice Over IP phone that provides me with an extension on the telephone system at head office. It allows them to pester me at home more easily, so I’m well aware of that device.
But I’m still left with questions.
There are several devices with names that don’t mean anything to me all. Liteon technology and Elitegroup Computer systems, for example.
I have (way) more than one Raspberry PI. How many are connected to the network will always vary because they’re continually swapped in and out of duty as they get re-imaged and re-purposed. But definitely, there should be more than one showing up.
There are a couple of devices marked as Unknown. Obviously, they’ll need looking into.
Perform a Deeper Scan
If we remove the -sn option nmap will also try to probe the ports on the devices. Ports are numbered endpoints for network connections on devices. Consider an apartment block. All the apartments have the same street address (the equivalent of the IP address), but each apartment has its own number (the equivalent of the port).
Each program or service within a device has a port number. Network traffic is delivered to an IP address and a port, not just to an IP address. Some port numbers are preallocated, or reserved. They are always used to carry network traffic of a specific type. Port 22, for example, is reserved for SSH connections and port 80 is reserved for HTTP web traffic.
We are going to use nmap to scan the ports on each device and tells which ones are open.
nmap 192.168.4.0/24
This time we’re getting a more detailed summary of each device. We’re told there are 13 active devices on the network. Wait a minute; we had 15 devices a moment ago.
The number of devices may well vary as you run these scans. It is likely due to mobile devices arriving and leaving the premises, or equipment being turned on and off. Also, be aware that when you switch on a device that has been powered off, it might not have the same IP address as it did the last time it was in use. it might, but it might not.
There was a lot of output. Let’s do that again and capture it in a file.
nmap 192.168.4.0/24 > nmap-list.txt
And now we can list the file with less, and search through it if we wish.
less nmap-list.txt
As you scroll through the nmap report you’re looking for anything that you can’t explain or that seems unusual. When you review your list, make a note of the IP addresses of any devices that you wish to investigate further.
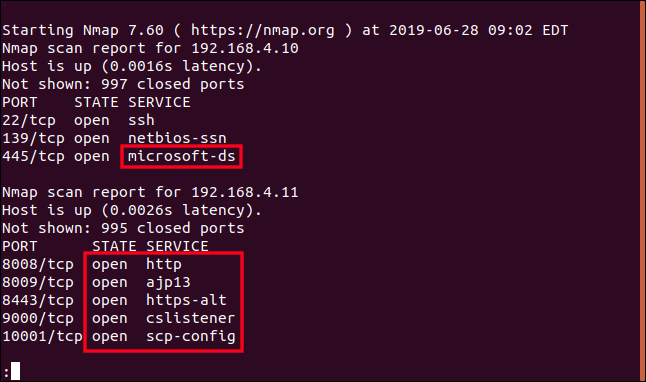
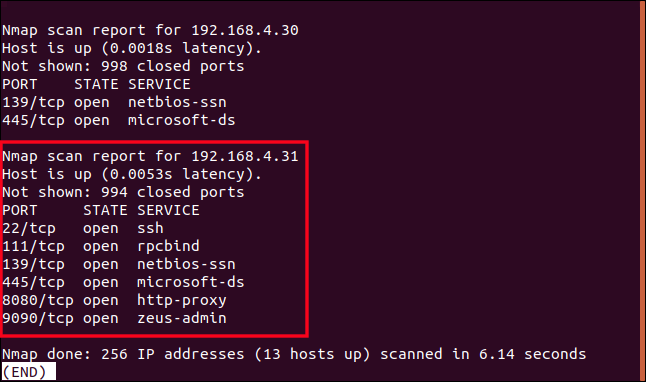
According to the list that we generated earlier, 192.168.4.10 is a Raspberry Pi. It will be running one Linux distribution or another. So what is using port 445? It is described as “microsoft-ds”. Microsoft, on a Pi running Linux? We’ll certainly be looking into that.
192.168.4.11 was tagged as “Unknown” in the earlier scan. It has a lot of ports open; we need to know what that is.
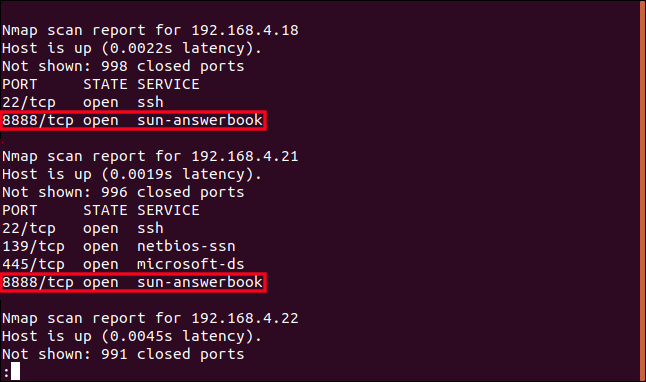
192.168.4.18 was also identified as a Raspberry Pi. But that Pi and device 192.168.4.21 both have port 8888 open, which is described as being used by “sun-answerbook”. Sun AnswerBook is a many-years retired (elementary) documentation retrieval system. Needless to say, I don’t have that installed anywhere. That needs looking at.
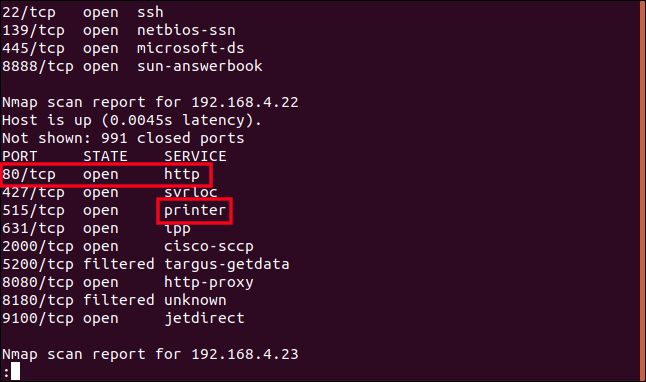
Device 192.168.4.22 was identified earlier as a Samsung printer, which is verified here by the tag that says “printer”. What caught my eye was the HTTP port 80 being present and open. This port is reserved for website traffic. Does my printer incorporate a website?
Device 192.168.4.31 is reportedly manufactured by a company called Elitegroup Computer Systems. I’ve never heard of them, and the device has a lot of ports open, so we’ll be looking into that.
The more ports a device has open, the more chances a cybercriminal has of getting into it — if it is exposed directly to the Internet that is. It’s like a house. The more doors and windows you have, the more potential points of entry a burglar has.
We’ve Lined Up The Suspects; Let’s Make Them Talk
Device 192.168.4.10 is a Raspberry Pi that has port 445 open, which is described as “microsoft-ds.” A quick bit of Internet searching reveals that port 445 is usually associated with Samba. Samba is a free software implementation of Microsoft’s Server Message Block protocol (SMB). SMB is a means of sharing folders and files across a network.
This makes sense; I use that particular Pi as a sort of mini-Network Attached Storage device (NAS). It uses Samba so that I can connect to it from any computer on my network. Ok, that was easy. One down, several more to go.
Unknown Device With Many Open Ports
The device with IP Address 192.168.4.11 had an unknown manufacturer and a lot of ports open.
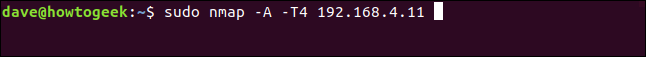
We can use nmap more aggressively to try to winkle more information out of the device. The -A (aggressive scan) option forces nmap to use operating system detection, version detection, script scanning, and traceroute detection.
The -T (timing template) option allows us to specify a value from 0 to 5. This sets one of the timing modes. The timing modes have great names: paranoid (0), sneaky (1), polite (2), normal (3), aggressive (4), and insane (5). The lower the number, the less impact nmap will have on the bandwidth and other network users.
Note that we’re not providing nmap with an IP range. We’re focussing nmap on a single IP address, which is the IP address of the device in question.
sudo nmap -A -T4 192.168.4.11
On the machine used to research this article, it took nine minutes for nmap to execute that command. Don’t be surprised if you have to wait a while before you see any output.
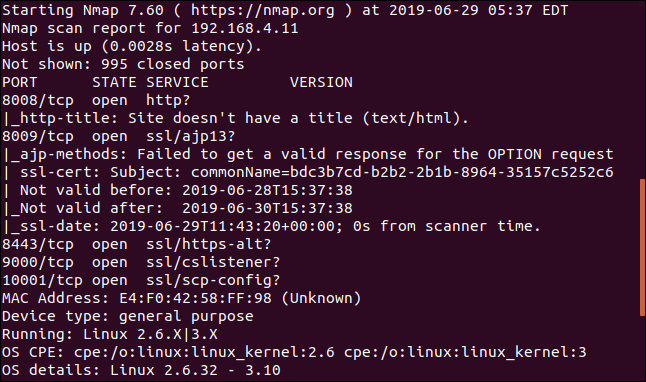
Unfortunately, in this case, the output doesn’t give us the easy answers we’d hoped for.
One extra thing we have learned is that it is running a version of Linux. On my network that isn’t a great surprise, but this version of Linux is odd. It seems to be quite old. Linux is used within almost all of the Internet of Things devices, so that might be a clue.
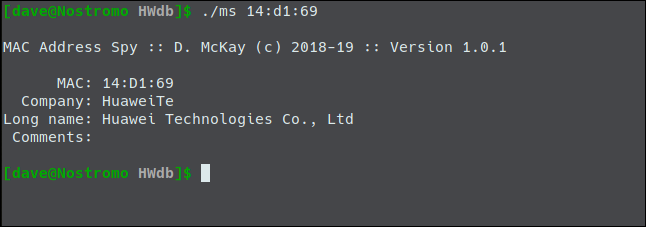
Further down in the output nmap gave us the Media Access Control address (MAC address) of the device. This is a unique reference that is assigned to network interfaces.
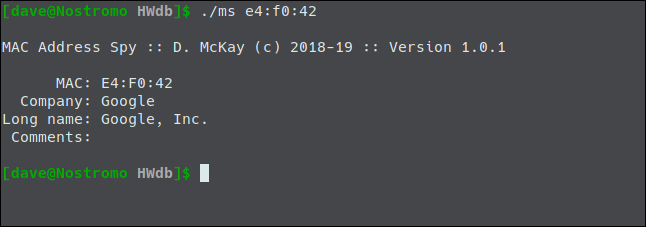
The first three bytes of the MAC address is known as the Organizationally Unique Identifier (OUI). This can be used to identify the vendor or manufacturer of the network interface. If you happen to be a geek who has put together a database of 35,909 of them, that is.
My utility says it belongs to Google. With the earlier question about the peculiar version of Linux and the suspicion that it might be an Internet of Things device, this points the finger fairly and squarely at my Google Home mini smart speaker.
You can do the same sort of OUI lookup online, using the Wireshark Manufacturer Lookup page.
Encouragingly, that matches my results.
One way to be certain about the id of a device is to perform a scan, turn the device off and scan again. The IP address that is now missing from the second set of results will be the device you just powered off.
Sun AnswerBook?
The next mystery was the “sun-answerbook” description for the Raspberry Pi with IP address 192.168.4.18. The same “sun-answerbook” description was showing up for the device at 192.168.4.21. Device 192.168.4.21 is a Linux desktop computer.
nmap makes its best guess at the use of a port from a list of known software associations. Of course, if any of these port associations are no longer applicable — perhaps the software is no longer in use and has gone end of life — you can get misleading port descriptions in your scan results. That was likely the case here, the Sun AnswerBook system dates back to the early 1990’s, and is nothing more than a distant memory — to those who’ve even heard of it.
So, if it isn’t some ancient Sun Microsystems software, so what could these two devices, the Raspberry Pi and the desktop, have in common?
Internet searches didn’t bring anything back that was useful. There were a lot of hits. It seems anything with a web interface that doesn’t want to use port 80 seems to opt for port 8888 as a fallback. So the next logical step was to try to connect to that port using a browser.
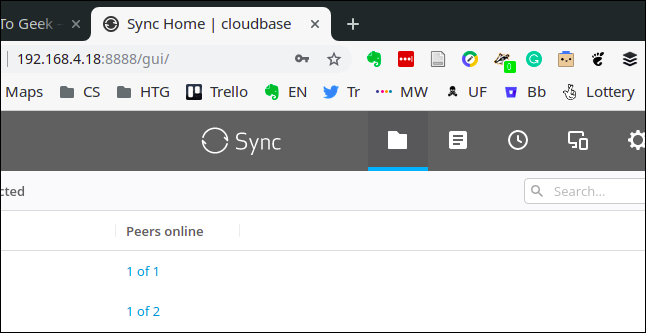
I used 192.168.4.18:8888 as an address in my browser. This is the format to specify an IP address and a port in a browser. Use a colon : to separate the IP address from the port number.
A web site did indeed open up.
It is the admin portal for any devices that are running Resilio Sync.
I always use the command line, so I’d completely forgotten about this facility. So the Sun AnswerBook entry listing was a complete red herring, and the service behind port 8888 had been identified.
A Hidden Web Server
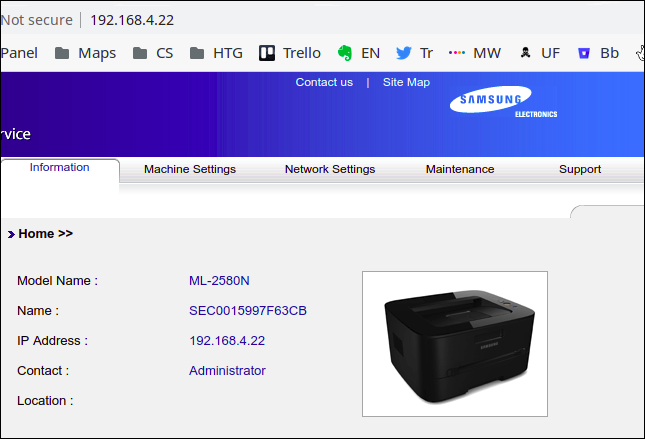
The next issue I’d recorded to take a look at was the HTTP port 80 on my printer. Again, I took the IP address from the nmap results and used it as an address in my browser. I didn’t need to provide the port; the browser would default to port 80.
Lo and behold; my printer does have an embedded web server in it.
Now I can see the number of pages that have been through it, the level of toner, and other useful or interesting information.
Another Unknown Device
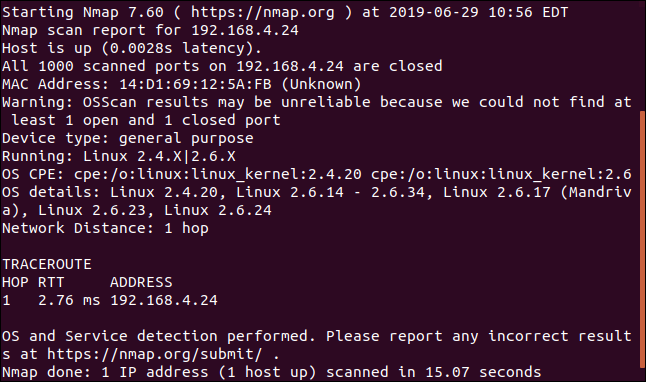
The device at 192.168.4.24 didn’t reveal anything to any of the nmap scans we’ve tried so far.
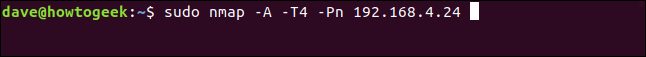
I added in the -Pn (no ping) option. This causes nmap to assume the target device is up and to proceed with the other scans. This can be useful for devices that don’t react as expected and confuse nmap into thinking they are off-line.
sudo nmap -A -T4 -Pn 192.168.4.24
This did retrieve a dump of information, but there was nothing that identified the device.
It was reported to be running a Linux kernel from Mandriva Linux. Mandriva Linux was a distribution that was discontinued back in 2011. It lives on with a new community supporting it, as OpenMandriva.
Another Internet of Things device, possibly? probably not — I only have two, and they’ve both been accounted for.
A room by room walk-through and a physical device count gained me nothing. Let’s look up the MAC address.
So, it turns out it was my mobile phone.
Remember that you can do these lookups online, using the Wireshark Manufacturer Lookup page.
Elitegroup Computer Systems
The last two questions I had were about the two devices with manufacturer names that I didn’t recognize, namely Liteon and Elitegroup Computer Systems.
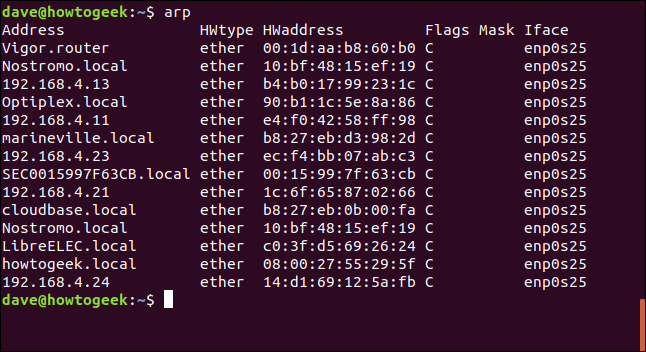
Let’s change tack. Another command that is useful in pinning down the identity of the devices on your network is arp. arp is used to work with the Address Resolution Protocol table in your Linux computer. It is used to translate from an IP address (or network name) to a MAC address.
If arp is not installed on your computer, you can install it like this.
On Ubuntu, use apt-get :
sudo apt-get install net-tools
On Fedora use dnf :
sudo dnf install net-tools
On Manjaro use pacman :
sudo pacman -Syu net-tools
To get a list of the devices and their network names — if they’ve been assigned one — just type arp and press Enter.
This is the output from my research machine:
The names in the first column are the machine names (also called hostnames or network names) that have been assigned to the devices. Some of them I have set (Nostromo, Cloudbase, and Marineville, for example) and some have been set by the manufacturer (such as Vigor.router).
The output gives us two means of cross-referencing it with the output from nmap. Because the MAC addresses for the devices are listed, we can refer to the output from nmap to further identify the devices.
Also, because you can use a machine name with ping and because ping displays the underlying IP address, you can cross-reference machine names to IP addresses by using ping on each name in turn.
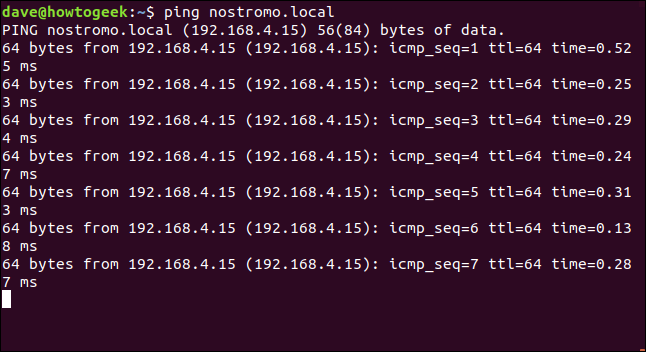
For example, let’s ping Nostromo.local and find out what its IP address is. Note that machine names are case-insensitive.
ping nostromo.local
You must use Ctrl+C to stop ping.
The output shows us that its Ip address is 192.168.4.15. And that happens to be the device that showed up in the first nmap scan with Liteon as the manufacturer.
The Liteon company makes computer components that are used by a great many computer manufacturers. In this case, it is a Liteon Wi-Fi card inside an Asus laptop. So, as we noted earlier, the name of the manufacturer that is returned by nmap is just its best guess. How was nmap to know the Liteon Wi-Fi card was fitted to an Asus laptop?
And finally. The MAC address for the device manufactured by Elitegroup Computer Systems matches the one in the arp listing for the device I have named LibreELEC.local.
This is an Intel NUC, running the LibreELEC media player. So this NUC has a motherboard from the Elitegroup Computer Systems company.
And there we are, all mysteries solved.
All Accounted For
We have verified that there are no inexplicable devices on this network. You can use the techniques described here to investigate your network either. You may do this out of interest — to satisfy your inner geek — or to satisfy yourself that everything connected to your network has a right to be there.
Remember that connected devices come in all shapes and sizes. I spent some time going around in circles and trying to track down a strange device before realizing that it was, in fact, the smartwatch on my wrist.
RELATED: Best Linux Laptops for Developers and Enthusiasts