Why You Must Stay Cybersecurity Conscious — Even at Home
In an age where our computers have become the nerve center of our personal and professional lives, cybersecurity is no longer just a concern for IT departments or large organizations. From online banking and confidential work documents to personal photos and messages, your PC stores a wealth of sensitive information. Unfortunately, unauthorized access can happen closer than you think — not just from hackers over the internet, but sometimes from someone physically using your computer without your permission.
Being cybersecurity conscious means staying alert to potential risks and knowing how to detect and respond to suspicious activity. It’s not just about installing antivirus software; it’s about actively understanding the tools your computer already provides to help you stay in control. Windows, for instance, comes equipped with a variety of built-in features designed to monitor activity, track recent file usage, and keep detailed event logs that can help you identify if someone else has accessed your device.
In this guide, we’ll explore step-by-step methods to check if your Windows PC has been used by another person — even when you weren’t around. These include:
-
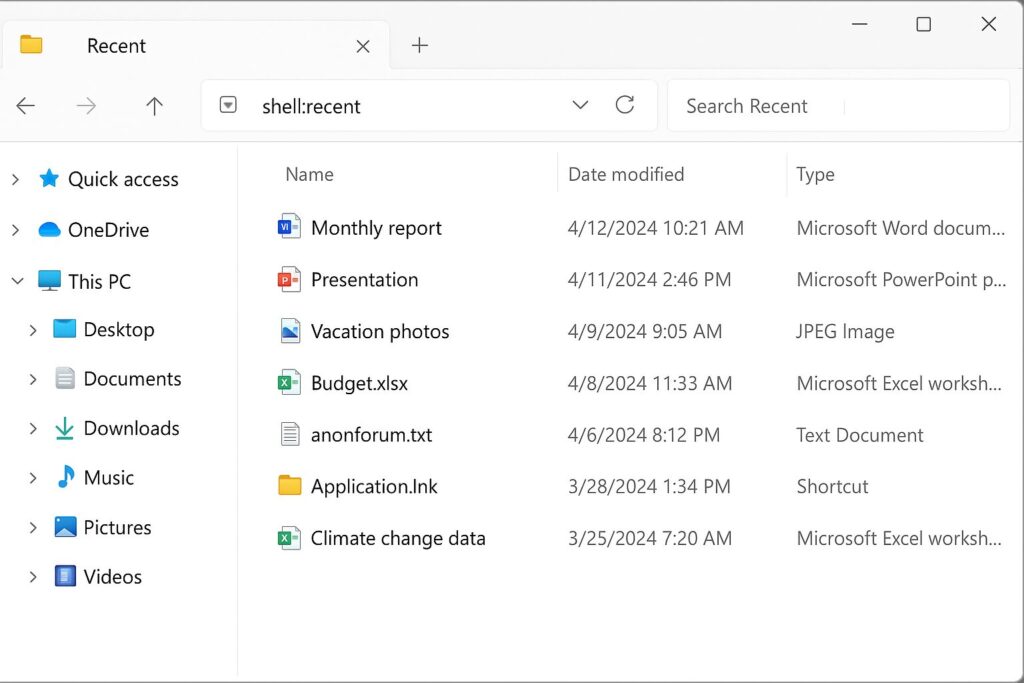
Checking recently opened files and applications using the Windows “shell:recent” command to view what’s been accessed.
-
Inspecting browser history with simple keyboard shortcuts to uncover any online activity you didn’t perform.
-
Reviewing recently installed programs to catch unfamiliar or suspicious software.
-
Using the Event Viewer’s Security Logs to pinpoint exact times your PC was turned on, logged into, or shut down.
These powerful, built-in Windows features serve as your first line of defense in personal cybersecurity. They allow you to audit your system, verify whether someone has tampered with it, and take appropriate action before any real damage is done.
Whether you’re a professional safeguarding work data, a parent protecting family privacy, or just a casual user wanting peace of mind, learning these steps will help you build a habit of digital vigilance — one of the most effective shields in today’s connected world.
What You’ll Need
-
A Windows PC (steps apply to Windows 10 and 11)
-
Your user account with administrator privileges (for Event Viewer and system checks)
-
About 10–20 minutes of your time
Step 1 — Check Recently Opened Files and Apps
-
Press Windows + R to open the Run dialog box.
-
Type:
and press Enter.
-
A File Explorer window will open, showing files and shortcuts that were opened recently under your user account.
-
Scan the list for unfamiliar files, folders, or applications and note their names and timestamps.
Why it matters:
This shows what files or applications have been accessed recently. It’s an easy way to spot if someone opened a document, photo, or app while you were away.
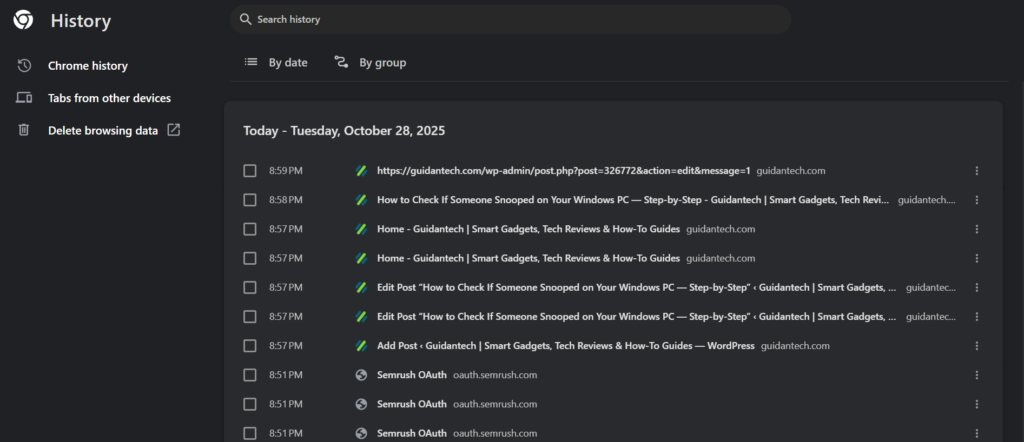
Step 2 — Inspect Browser History
-
Open your web browser (Microsoft Edge, Chrome, Firefox, etc.).
-
Press Ctrl + H to open the browsing history.
-
Review the list of websites and search queries for any activity you don’t recognize.
-
Remember that private/incognito mode will not display any record in this history.
Tip:
If you have multiple browsers installed, check each one. People often use a different browser to avoid detection.
Step 3 — Review Recently Installed Programs
-
Press the Windows key and type Programs and Features (or open Add or Remove Programs).
-
Sort the list by Install date.
-
Carefully check the most recent installations for unknown or suspicious software.
-
If you find something odd, search the program name online before uninstalling it to confirm whether it’s legitimate.
Why this helps:
Many times, snoopers or unauthorized users install small tools or apps — like file-sharing programs or screen recorders — to monitor activity. Reviewing installation dates can help you spot these early.
Step 4 — Use Event Viewer to Check Login Activity
Administrator access may be required for this step.
-
Press Windows + X and select Computer Management.
-
In the left sidebar, expand Event Viewer → Windows Logs → Security.
-
Look for Audit Success or Audit Failure events related to logon (Event ID 4624 indicates a successful logon).
-
Check timestamps to identify when your PC was turned on, accessed, or shut down.
Why it’s important:
The Event Viewer logs are extremely detailed. They can show exactly when someone logged into or used your PC, helping you verify if activity occurred while you were away.
Step 5 — Combine and Analyze Your Findings
Once you’ve checked all the above:
-
Note the timestamps from each section — recent files, browser history, installations, and Event Viewer logs.
-
Create a simple timeline showing when and how your PC was accessed.
-
If something suspicious appears, it’s time to act quickly.
What to Do If You Find Evidence of Tampering
If you discover unauthorized access or strange activity:
-
Change your passwords immediately (Windows account, email, social media, and banking apps).
-
Use another device for password changes to avoid further compromise.
-
Run a full antivirus and antimalware scan (use Windows Defender or trusted software like Malwarebytes).
-
Uninstall any suspicious programs that you verified are unsafe.
-
Back up your important files to an external drive or cloud service.
-
If the intrusion appears severe (e.g., your data was accessed or stolen), consider reinstalling Windows to start fresh.
-
For workplace or legal implications, notify your IT department or law enforcement immediately.
Prevention Tips — Stay Secure Going Forward
-
Always lock your screen before stepping away: press Windows + L.
-
Use a strong password or PIN and enable Windows Hello for biometric login if available.
-
Set automatic screen timeout and require sign-in upon wake.
-
Create a guest account for others who need to use your PC.
-
Keep your Windows updates and antivirus active.
-
Consider enabling BitLocker encryption to protect data from unauthorized physical access.
-
Run periodic audits (e.g., check
shell:recentor Event Viewer logs once a month).
Quick One-Page Checklist
-
Checked recent files (
shell:recent) -
Reviewed browser history (
Ctrl + H) -
Verified recent installations (Programs and Features)
-
Checked login activity (Event Viewer → Security Logs)
-
Changed passwords and ran antivirus scan
-
Backed up important files
Cybersecurity isn’t only about firewalls or antivirus software — it’s also about awareness and vigilance. Windows provides powerful built-in tools that, when used properly, help you monitor, detect, and respond to unauthorized access.
By making these checks a regular habit, you’re not just protecting your files; you’re reinforcing your digital independence — ensuring that every click, login, and activity on your PC is truly yours.