
We already know that iOS 17.4 will be a game-changing update for the iPhone, with support for alternative app stores and payments in the EU, a handful of new emoji, and virtual numbers for Apple Cash cards, but Apple has one more feature in store when it launches sometime over the next few weeks. In a post on its Security Research blog, Apple has outlined a new state-of-the-art security upgrade for iMessage that “has the strongest security properties of any at-scale messaging protocol in the world.”
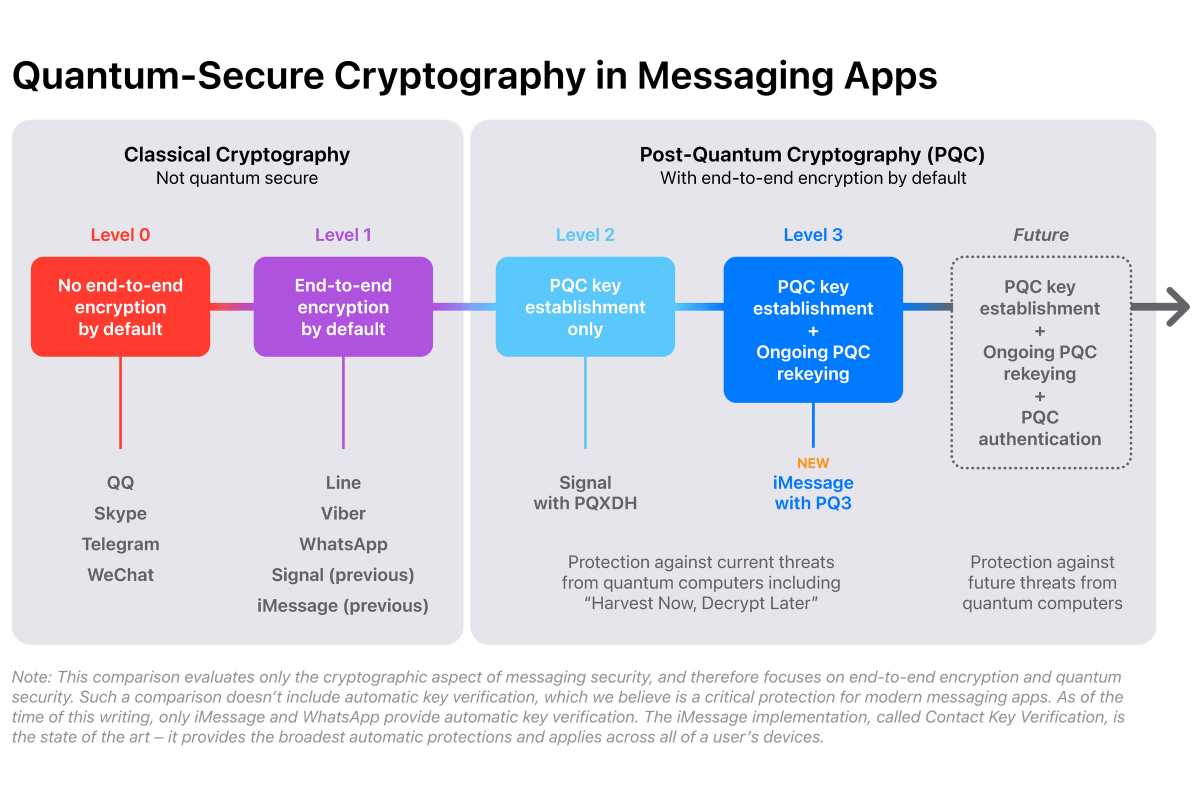
It’s all very technical, but Apple will be deploying post-quantum cryptography Level 3 (PQ3), which “is used to secure both the initial key establishment and the ongoing message exchange, with the ability to rapidly and automatically restore the cryptographic security of a conversation even if a given key becomes compromised.” That means a hacker would need to crack two symmetric keys that go beyond any of the available methods used in even the most highly sophisticated attacks.
Apple
Apple notes that Signal was the first large-scale messaging service to use post-quantum cryptography with the recent addition of PQXDH support, which elevated the app’s security from Level 1 to Level 2. However, Apple says iMessage’s new PQ3 protocol takes it a step further Here’s how Apple describes the protocol in action:
When Alice’s device instantiates a new session with Bob’s device, her device queries the IDS server for the key bundle associated with Bob’s device. The subset of the key bundle that contains the device’s authentication key and versioning information is validated using Contact Key Verification. The device then validates the signature covering the encryption keys and timestamps, which attests that the keys are valid and have not expired.
Alice’s device can then use the two public encryption keys to share two symmetric keys with Bob. The first symmetric key is computed through an ECDH key exchange that combines an ephemeral encryption key from Alice with Bob’s registered P-256 public key. The second symmetric key is obtained from a Kyber key encapsulation with Bob’s post-quantum public key.
This combination ensures that the initial session state cannot be derived without knowing both of the shared secrets, meaning an attacker would need to break both algorithms to recover the resulting secret, thus satisfying our hybrid security requirement.
iMessage has been used in high-level zero-click government attacks, most notably Israeli NSO Group’s spy software Pegasus. Apple says the new system is essential for safeguarding against known and unknown future attacks and will protect against agents who have already collected encrypted data for future decryption.
Apple says the new protocol will start to roll out with the public releases of iOS 17.4, iPadOS 17.4, macOS 14.4, and watchOS 10.4, and is already in the developer and public beta releases.






