Built around various Arm cores with added security to protect stored intellectual property, they are intended to run AI algorithms locally in battery-powered devices.
“There are many Edge ML applications that require 50 to 250Gop/s to become useful,” said Alif marketing v-p Mark Rootz. “Typical 32bit MCUs can’t come close to that performance level, so to find a solution developers had to jump all the way to GPU-based accelerators at about the 1,000Gop/s level, which is over-kill in power, size, cost and complexity. Alif fills this gap in the middle, the sweet spot for battery-powered products on the edge.”
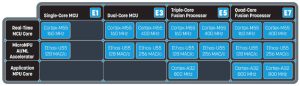 There are four levels of Ensemble ICs, with a mix of Arm Cortex-M55 MCU, Cortex-A32 MPU and Ethos-U55 neural processing cores.
There are four levels of Ensemble ICs, with a mix of Arm Cortex-M55 MCU, Cortex-A32 MPU and Ethos-U55 neural processing cores.
- E1 single core
160MHz Cortex-M55
128MAC/c Ethos-U55 - E3 dual core
160MHz Cortex-M55
400MHz Cortex-M55
128mac/c Ethos-U55
256mac/c Ethos-U55 - E5 Linux-capable triple core
160MHz Cortex-M55
400MHz Cortex-M55
128mac/c Ethos-U55
256mac/c Ethos-U55
800MHz Cortex-A32 - E7 Linux-capable quad core
160MHz Cortex-M55
400MHz Cortex-M55
128mac/c Ethos-U55
256mac/c Ethos-U55
2x 800MHz Cortex-A32
For one inference of image classification (MobileNet V2 1.0), the company claims that its M55 + U55 core combination is 800x faster than a “previous gen Cortex-M”, 78x faster than an M55 core alone (8 vs 624ms) and 76x more energy efficient (3 vs 228mJ) than an M55 alone.
Picking the E1 series as an example, which is aimed at wearables, its peripherals include: dual-lane MIPI-DSI for displays, multiple microphone and audio inputs, and SAR and 24bit ΔΣ ADCs.
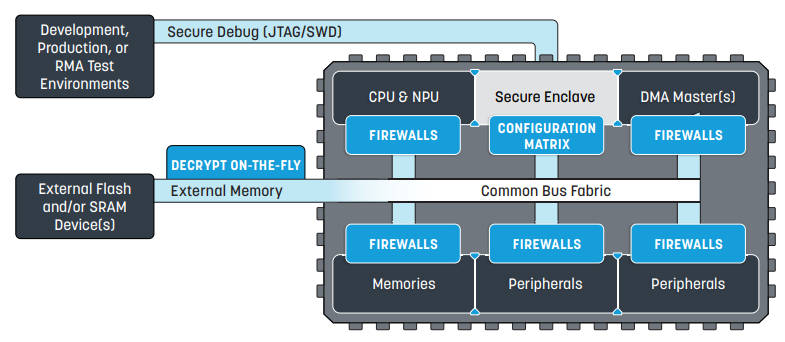
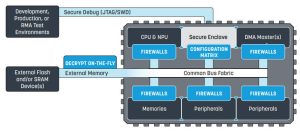
On security, the company said: “Security is a cornerstone of every device, where an isolated portion of the chip manages a strict security policy throughout its entire life-cycle. Application code and machine learning models are safe from IP theft through robust readout prevention, plus code originality and integrity are preserved to prevent malware attacks. Secret and private data on the device and over communication channels are shielded from malicious access by means of extensive cryptography.”
The secure enclave include a root-of-trust for secure boot, a unique ID, key generation, key storage, a dedicated security processor, dedicated protected memory and hardware cryptographic acceleration, and then there are “configurable firewalls that regulate access of each CPU to sections of memories and individual peripherals, and extend the capabilities of the standard Arm TrustZone security partitioning”, said Alif.
During manufacture, the devices are in a provisioning state when all parts can be accessed and changes are reversible. For deployment, the on-board security sub-system takes charge to validate firmware signatures and manage over-the-air updates. There is also an end-of-life state where all secrets are erased for disposal.
An associated application kit is available to asses AI algorithm performance and power using live data collected by a camera and other sensors on the board.
Find the Ensemble AI MCU data sheets on this webpage








